HEADS-UP – Purview will starting April 1. 2023 be replacing the legacy OME way of encrypting outgoing mail from O365.
If you don’t do anything, Microsoft will process all mail flow rules that currently applies OME protection to Microsoft Purview Message Encryption protection.
This will bring a much more secure and flexible end-user experience, that differs depending on location and platform. There will also be other major improvements, like the ability to customize Mail body branding with your companys logo etc, to give a more trustworthy experience for recipients.
Use the commandlet Set-OMEConfiguration to adjust the branded experience
https://learn.microsoft.com/en-us/powershell/module/exchange/Set-OMEConfiguration?view=exchange-ps
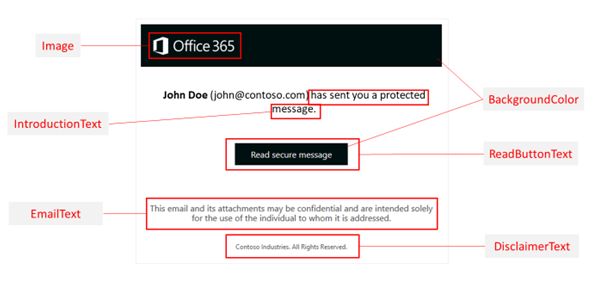
With legacy OME encryption the behaviour differs, depending on platform, client, locations etc – where this is much more streamlined with Purview.
Below is a comparison chart
| Situation | Legacy OME | IRM in AD RMS | Microsoft Purview Message Encryption |
| Sending an encrypted mail | Through Exchange mail flow rules | End-user initiated from Outlook desktop or Outlook on the Web; or through Exchange mail flow rules | End-user initiated from Outlook desktop, Outlook for Mac, or Outlook on the Web; through Exchange mail flow rules (also known as transport rules) and data loss prevention (DLP) |
| Rights management template | N/A | Do Not Forward option and custom templates | Do Not Forward option, encrypt-only option, and custom templates |
| Recipient type | Internal and external recipients | Internal recipients only | Internal and external recipients |
| Experience for internal recipient | Recipients receive an HTML message, which they download and open in a web browser or mobile app | Native inline experience in Outlook clients | Native inline experience for recipients in the same organization using Outlook clients. Recipients can read message from OME portal using clients other than Outlook (no download or app required). |
| Experience for external recipient | Recipients receive an HTML message, which they download and open in a web browser or mobile app | N/A | Native inline experience for Microsoft 365 recipients. All other recipients can read message from OME portal (no download or app required). |
| Attachment permissions | No restrictions on attachments | Attachments are protected | Attachments are protected for the Do Not Forward option and custom templates. Admins can choose whether attachments for the encrypt-only option are protected or not. |
| Bring your own key (BYOK) support | None | None | BYOK supported |
What you need to do to prepare:
If you want to compare the behavior before the deprecation, you can modify and test the changes with your mail flow rules by following the steps outlined in this documentation: Define mail flow rules to use Microsoft Purview Message Encryption
OUTLOOK on the web – manual use
As more and more users start using Outlook directly on the web – also please take note of the ability to add ENCRYPT button for ease of use
Run the Set-IRMConfiguration cmdlet with the -SimplifiedClientAccessEnabled parameter:
Set-IRMConfiguration -SimplifiedClientAccessEnabled <$true|$false>
For example, to disable the Encrypt button:
Set-IRMConfiguration -SimplifiedClientAccessEnabled $false
To enable the Encrypt button:
Set-IRMConfiguration -SimplifiedClientAccessEnabled $true
Automated use
Most likely you want to automate encryption either based on content or labelling, there are many ways to achieve this – most prominent being either by means of a mailflow rule in the Exchange admin center.
You can have the mailflow rule kick in when specific words or phrases are used.:
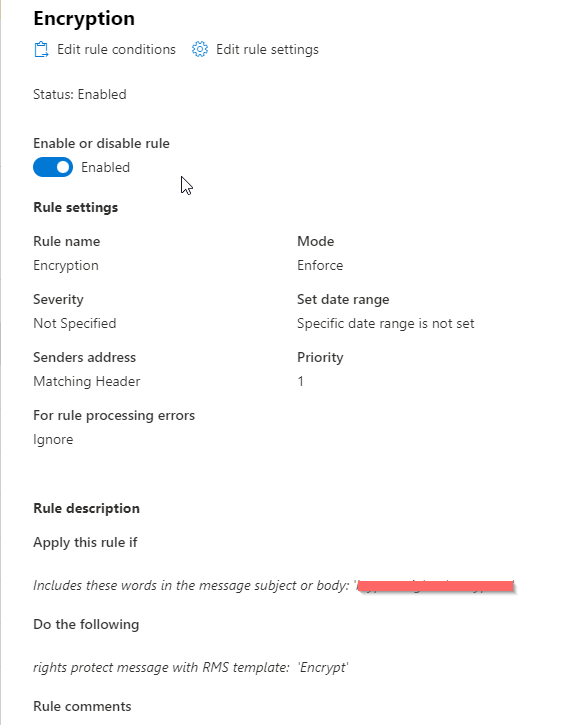
OR you can use automation be means of sensitivity labelling.
As an example in this Label example i want to auto encrypt all content that contains at least 10 US Bank account numbers.
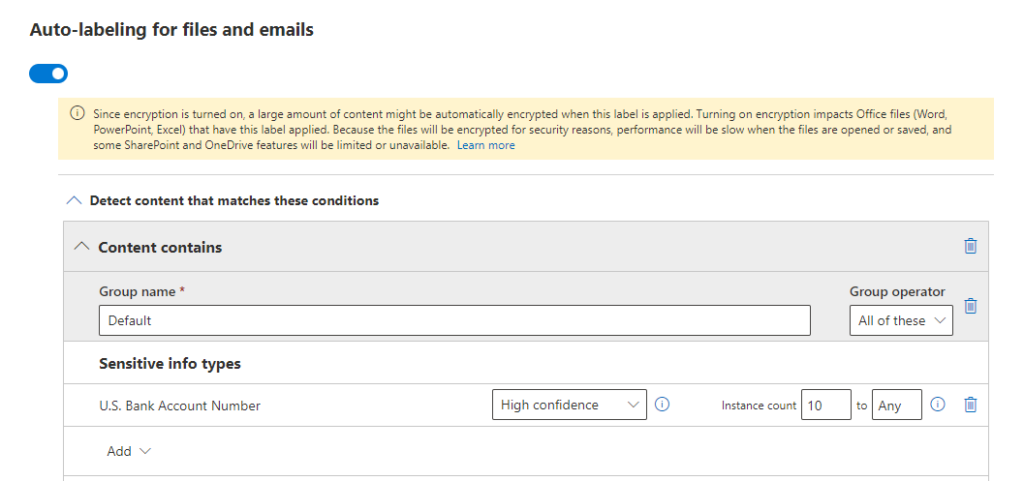
And i want to adjust the number of days in which the content will be available without authentication (offline access)
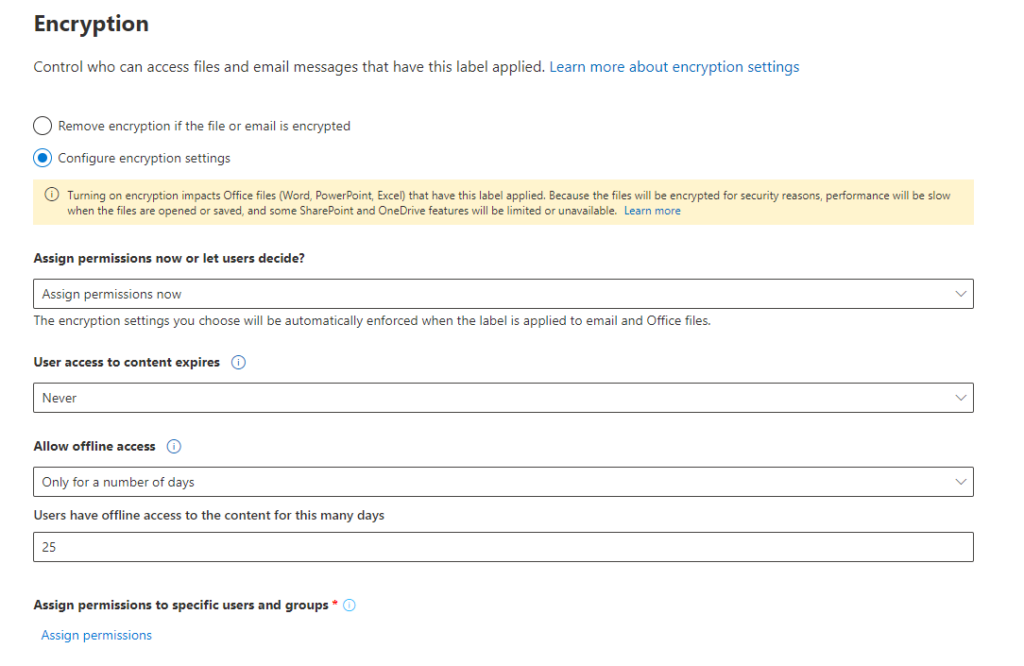
Giving me this Label, that i can the publish with a Labelling policy
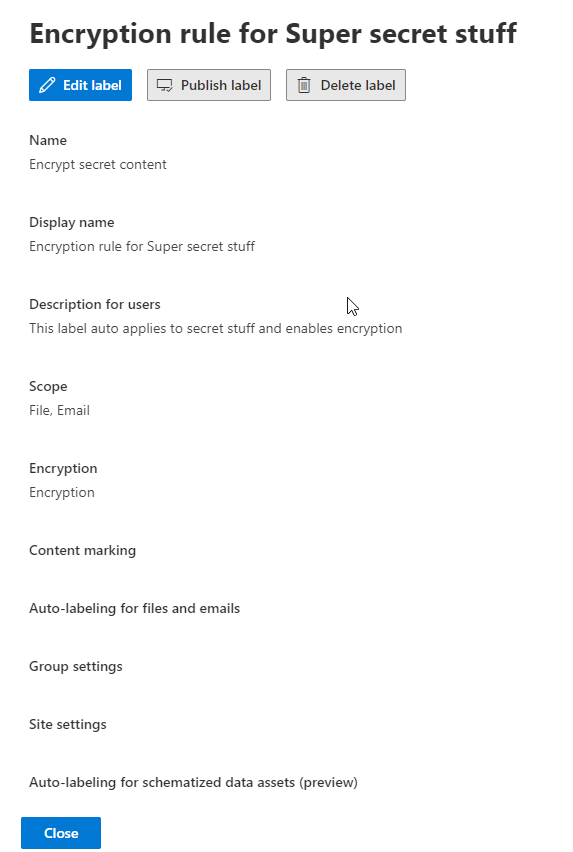
For details on Labels and label policyes please refer to the official documentation that gives great explanations and examples.
Foundation
To get everything up and running you need sufficient licenses – and you will have to make sure that Azure rights management is enabled in your tenant.
To use Microsoft Purview Message Encryption, you need one of the following plans:
- Microsoft Purview Message Encryption is offered as part of Office 365 Enterprise E3 and E5, Microsoft 365 Enterprise E3 and E5, Microsoft 365 Business Premium, Office 365 A1, A3, and A5, and Office 365 Government G3 and G5. You don’t need additional licenses to receive the new protection capabilities powered by Azure Information Protection.
- You can also add Azure Information Protection Plan 1 to the following plans to receive Microsoft Purview Message Encryption: Exchange Online Plan 1, Exchange Online Plan 2, Office 365 F3, Microsoft 365 Business Basic, Microsoft 365 Business Standard, or Office 365 Enterprise E1.
- Each user benefiting from Microsoft Purview Message Encryption needs to be licensed to be covered by the feature.
You can verify that your Microsoft 365 tenant is properly configured to use Microsoft Purview Message Encryption in Exchange Online PowerShell.
- Connect to Exchange Online PowerShell using an account with global administrator permissions in your Microsoft 365 tenant.
- Run the Get-IRMConfiguration cmdlet.You should see a value of
$Truefor the AzureRMSLicensingEnabled parameter, which indicates that Microsoft Purview Message Encryption is configured in your tenant. If it is not, use Set-IRMConfiguration to set the value of AzureRMSLicensingEnabled to$Trueto enable Microsoft Purview Message Encryption. - Run the Test-IRMConfiguration cmdlet using the following syntax:
Test-IRMConfiguration -Sender tjo@juhlconsult.dk -Recipient someoneelse@juhlconsult.dk
For sender and recipient, use the email address of any user in your Microsoft 365 tenant.
Results : Acquiring RMS Templates …
– PASS: RMS Templates acquired. Templates available: Juhl – Confidential View Only, Juhl – Confidential, Do Not Forward.
Verifying encryption …
– PASS: Encryption verified successfully.
Verifying decryption …
– PASS: Decryption verified successfully.
Verifying IRM is enabled …
– PASS: IRM verified successfully.
OVERALL RESULT: PASSIf the test fails with an error message Failed to acquire RMS templates, execute the following commands and run the Test-IRMConfiguration cmdlet to verify that it passes. Connect to the AIPService module to run the cmdlet.
$RMSConfig = Get-AipServiceConfiguration $LicenseUri = $RMSConfig.LicensingIntranetDistributionPointUrl Set-IRMConfiguration -LicensingLocation $LicenseUri Set-IRMConfiguration -InternalLicensingEnabled $true
I hope this can be a teaser to start your journey into Purview – its super powerfull.
LINKS and HELP
Intro to Purivew: https://learn.microsoft.com/en-us/azure/purview/overview
Encryption in general info: https://learn.microsoft.com/en-us/microsoft-365/compliance/encryption?view=o365-worldwide
Manage Message encryption: https://learn.microsoft.com/en-us/microsoft-365/compliance/manage-office-365-message-encryption?view=o365-worldwide
Double Key encryption: https://utimaco.com/solutions/applications/double-key-encryption
Sensitivity labels: https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Using labels in Groups, Teams and Sharepoint sites: https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teams-groups-sites?view=o365-worldwide




